
One of the vital layers of IT security safeguards is your employees. Your users are on the front line of cyberattacks that come in via phishing emails in their inboxes every day.
Approximately 1 in every 99 emails is a phishing attack, and all it takes is one wrong click to infect a company network with malware or cause a major costly data breach.
To ensure that a network security strategy is going to keep your business fully protected, it needs to incorporate ongoing employee security awareness training. This keeps teams up to date on the newest threats to watch out for and helps them sharpen their phishing detection skills.
A single phishing email can cost a company as much as $100,000.
Employee cybersecurity training also improves compliance efforts, reducing the risk of a compliance penalty. When employees are trained regularly on proper data handling, they not only get important reminders of best practices, it also reinforces the importance of data security to their organization.
When conducting employee security awareness training, there are several key things that you should include.
A full 43% of employees aren’t aware that clicking on a suspicious link or opening a file attachment in an email is likely to cause a malware infection.
It’s important to train employees on the dangers of phishing emails and that links can be just as dangerous as file attachments. In fact, phishing scammers use links much more than file attachments because they can often get by antivirus mail filters.
Why Are URLs dangerous?
Phishing is getting more sophisticated and harder to tell from the real thing, but there are certain tactics that employees can use to identify a phishing email in their inbox.
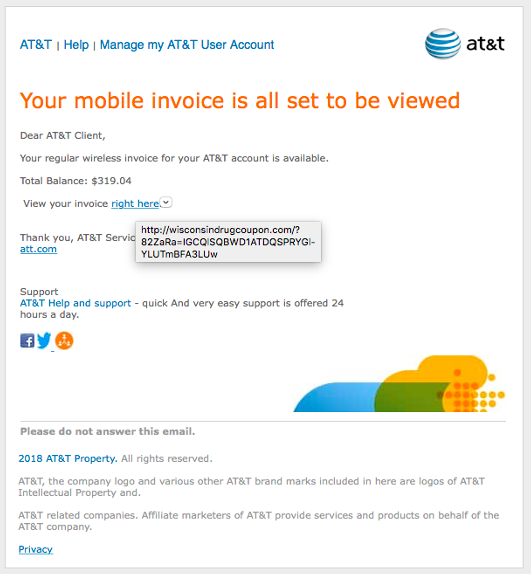
This phishing email is made to mimic that of AT&T, hovering over the link reveals it’s a fake.
One of the best ways to identify a phishing email is by hovering your cursor over any links in the email (text and image links). This will pop up a window that reveals the true URL, which is usually not one owned by the company that the phishing is trying to mimic.
Other ways to detect a phishing email are to ask these questions:
Password security is becoming a bigger problem that it already was because of the move to the cloud. The stealing of passwords is now the number one objective of phishing attacks because it’s much easier for hackers to get to company resources using a legitimate login than to try to hack the security of someone like Google, Amazon, or Microsoft.
Yet, many users still have bad password habits. These include:
Employees need to understand that their login is all that’s keeping a hacker from multiple vital company resources and that the use of things like multi-factor authentication and password managers can significantly increase account protection.
When cybersecurity incidents are caught right away, damage can often be mitigated. For example, if you realize right away that you’ve just put your credit card number into a fake phishing site, you can immediately contact your bank to block the card.
Cybersecurity mistakes can often get worse because an employee didn’t know what to do or kept quiet about a suspected download of malware because they were afraid to get in trouble.
It’s important to instruct employees of the immediate things to do if they even just suspect they may have encountered phishing or malware and possibly infected their device. You should also stress that it’s to mitigate damages and that they won’t get into trouble for reporting a cybersecurity incident when it happens, they’re actually doing their part to protect the company from a potential breach.
Many users, even those that are more computer savvy, get fooled by email spoofing. This is when a hacker uses a legitimate company’s domain name in the “From” email address.
A user might look up and see their own company’s domain or that of a vendor and be fooled into thinking the email is legitimate and taking a requested action.
Employees need to know that they can’t trust the address in the sender line and that these are often fakes. Looking at the raw message source (if they know how to do that) can reveal the true email address originating an email.
Haxxess can help your Northern Ontario company plan and implement an effective and ongoing employee security awareness training as part of a strong cybersecurity strategy.
Contact us today to schedule a free consultation! Call 705-222-8324 or reach out online.